Risk is the possibility of an act or event occurring that would have an adverse effect on the organization. Risk can also be the potential that a given threat will exploit vulnerabilities to cause loss of, or damage to, the organization. Risk is generally measured by a combination of severity and likelihood of occurrence.
A threat is an action or event that might jeopardize the organization. It is a sequence of circumstances and events that allow a human (disgruntled employee, etc.) or other agent (virus, Trojan horse, etc.) to cause a misfortune by exploiting vulnerabilities. A vulnerability is a weakness that allows a threat to manifest itself.


Considerations to keep in mind when determining threats:
- Determining the legal implications and contingent liability associated with any identified risks. For example, if hackers successfully access the organization’s Facebook account and use it to subsequently attack followers/friends, the organization may be liable for damages incurred by the party that is attacked.
- Capability and motivation are important attributes of threats. Threats need both attributes (capability and motivation) to be credible. For example, a skilled hacker seeking access to a Facebook account is considered a credible threat because the hacker has the capability (skills) and motivation (financial/ideological gain from the use of the organization's Facebook account).
- Interested parties. Serious hackers, interested computer novices, dishonest vendors or competitors, disgruntled current or former employees, organized crime rings or even agents of espionage pose a potential threat.
- Poor security program/poor employee security awareness. Hackers often exploit well-known weaknesses in creating secure passwords.
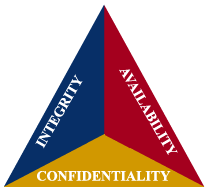
Internal controls are mechanisms that enable the organization to achieve its business objectives. With appropriate controls in place the organization is able to effectively mitigate the risk posed by a threat. With respect to social media, internal controls are designed to meet three main objectives:
- Confidentiality: Preventing the disclosure of sensitive information;
- Integrity: Preventing unauthorized modifications to information and maintaining internal and external consistency; and,
- Availability: Ensuring that the systems are working and that the data is accessible to users as required.
In addition to requiring the documentation of threats and vulnerabilities, the SMRAP also requires the documentation of associated controls. To maintain an effective social media risk assessment process the organization must ensure that the organization has adequately considered the implementation of the following types of controls:
- Preventative Controls: These controls are established to avoid occurrences of unwanted events. This type of control may include passwords, policies, procedures, security awareness program, etc. These controls are considered “proactive.”
- Detective Controls: These controls alert and identify violations after the fact. These controls can include social media monitoring and other information that provides notification after the event has occurred. These controls are considered “reactive.”
- Corrective Controls: These controls are intended to remedy unauthorized events and to restore the original controls. For example, the ability to reset the custodian of a social media account that has been locked-out due to some adverse event is considered a corrective control.
- Deterrent Controls: These controls discourage violations. For example, a policy statement that states that violators may be terminated for non-compliance with the social media policy is considered a deterrent control.
Part 4 of this series will begin discussion on the risk assessment process.
Nice blog! Very interesting and informative post….Thank's for sharing such a nice information….Keep it up!!
ReplyDeleteWeb Development in Gravesend
PHP Services in Gravesend
you are sharing good stuff about social media.
ReplyDeletebest haircuts for women over 60
Hi, I just gone through this blog, the information was really very valuable, would love to see more from you. i have also plenty of the same kind of content You can explore my blog by clicking the link below
ReplyDeleteBest digital marketing course in delhi
Advance digital marketing course in delhi
Advance digital marketing Institute in delhi
High Class digital marketing Institute in delhi
High Class digital marketing course in delhi